InfluxDB for Security Monitoring
The security monitoring solution using InfluxDB provides real-time monitoring, correlation, and expert analysis of activity in your environment, detecting and alerting valid threats to your data and devices.
#1
Time Series Database
Source: DB Engines
1B+
Downloads of InfluxDB
Take the complexity out of time series data management
Try InfluxDBTurn high-volume, high-velocity, high-resolution time series data into actionable intelligence without sacrificing performance.
Get high-speed ingestion, real-time querying, and seamless scalability in a highly performant time series database that can handle unlimited volumes of time series data, even as data complexity and cardinality increases.
Run InfluxDB at scale in any environment in the cloud, on-premises, or at the edge. InfluxDB consists of the core database and storage engine, an API, and an ecosystem of tools and integrations to manage time-stamped data. Easily integrate with 5K+ prebuilt connections using Telegraf, our open source agent with 5B+ downloads.
Run InfluxDB 3 where you need it
Start for free, scale in seconds
Start NowFor small workloads and getting started
Deploy anywhere: on-prem, private cloud, edge, or multi-tenant cloud.
Secure, dedicated cloud infrastructure
Run a Proof of ConceptFor scaled workloads
Fully-managed, single-tenant service with unlimited scale, high availability, secure private connections, and enhanced Support.
Own your data with enterprise features
Run a Proof of ConceptFor scaled workloads
Control your infrastructure with unlimited scale, high availability, enterprise-grade security, and enhanced Support. On-prem, private cloud, and edge deployment.
Why InfluxDB
Limitless data collection
Ingest and analyze millions of time series data points per second without limits or caps.
Predict and prevent
Maximize uptime and prevent costly failures with real-time monitoring and preventative insights.
Real-time query
Data is immediately available for querying in InfluxDB, enabling real-time SQL queries and lightning-fast responses.
What is security event monitoring?
Security event monitoring provides real-time monitoring, correlation, and expert analysis of activity in your environment, detecting and alerting valid threats to your data and devices.
Why InfluxDB for security event monitoring?
Security monitoring is complex. Successful implementation of a security monitoring infrastructure involves people, processes, technology, and data and requires multiple iterative phases to reach maturity. The data component comes from consuming log files from every possible asset, be it an application, database, virtual machine, operating system, server, network component, storage, or even intelligent power strips. Log data from these assets will help with the following:
- Identifying security incidents
- Monitoring policy violations
- Establishing baselines
- Assisting non-repudiation controls
- Providing information about problems and unusual conditions
- Contributing additional application-specific data for incident investigation which is lacking in other log sources
- Helping defend against vulnerability identification and exploitation through attack detection
But log data on its own is not an efficient way of finding the anomalies and therefore, this data should be collected and organized in a collection of time series. This data set provides a way to correlate time series events that enable incident detection, response, remediation and forensics workflows to be timely and successful.
Related resources for developers
InfluxDB Integrations
Free InfluxDB training
“When information is gathered from a large number of devices out at the edge, ensuring that data is reliable and trustworthy can be challenging. Ockam provides open source tools and libraries that make it easy to establish and maintain mutually authenticated secure channels between fleets of globally distributed devices and InfluxDB."
Mrinal WadhwaCTO, Ockam
Open data standards drive performance and interoperability
InfluxDB 3 is built in Rust and the FDAP stack—Flight, DataFusion, Arrow, and Parquet—leveraging Apache-backed technologies to efficiently ingest, store, and analyze time series data at any scale.
Get InfluxDBF
Flight for efficient columnar data transfer

D
DataFusion for high-performance querying
A
Arrow for optimized in-memory columnar analytics

P
Parquet for high-compression storage
InfluxDB’s columnar database supports time series data at a lower TCO
See ways to get started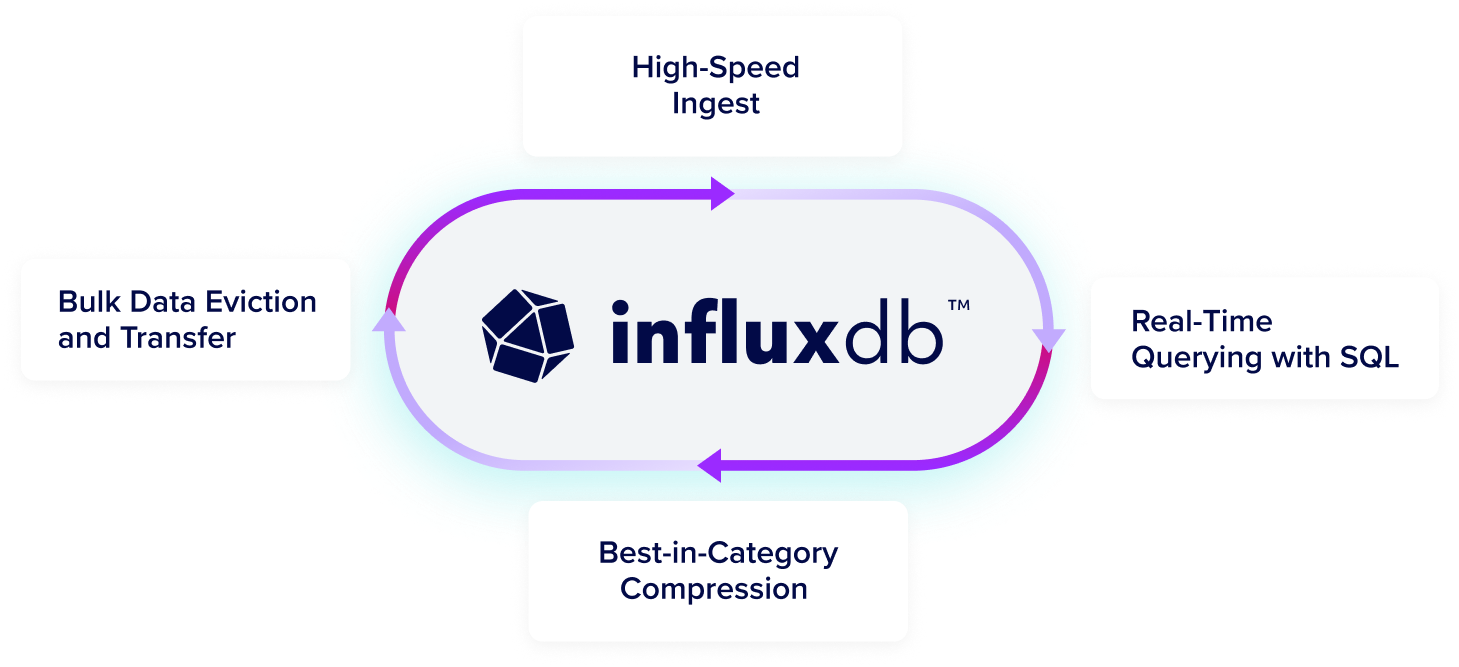
Loved by developers, trusted by enterprises
65M+
daly events processed
45x
more resource efficient
Siemens Energy
“[We] long used InfluxDB open source... Moving to commercial InfluxDB was a strategic move to unify our data infrastructure, ensuring we have the reliability, scalability, and real-time performance to keep pace with production... and proactive maintenance.”
Jan Petersen
Senior Manufacturing Engineer
500M+
Metrics collected daily
Mission-critical monitoring
Real-time data access for queries
LOFT ORBITAL
Space Made Simple: How Loft Orbital Delivers Unparalleled Speed-to-Space with InfluxDB Cloud
Read Case Study65M+
daly events processed
45x
more resource efficient
CAPITAL ONE
"InfluxDB is a high-speed read and write database. The data is written in real-time, you can read it in real-time, and while reading, you can apply your machine learning model. So, in real-time, you can forecast and detect anomalies."
Rajeev Tomer
Sr. Manager of Data Engineering
50%
lower total cost of ownership
100K
real-time metrics with simplified deployment
TERÉGA
Teréga Replaced Its Legacy Data Historian with InfluxDB
Lorem ipsum
Lorem ipsum dolor sit amet consectetur.
65M+
daly events processed
45x
more resource efficient
WIDEOPENWEST
"I was blown away with how easy it was to install and configure InfluxDB. The clustering was easy. The documentation was great, and the support has been second to none."
Dylan Shorter
Engineer III, Software and Product Integration Engineering
45%
Less equipment downtime
10%
Reduced waste
MAJIK SYSTEMS
From Reactive to Proactive: How MAJiK Systems Embraced Predictive Maintenance with InfluxDB and Time Series Data
Dylan Shorter
Engineer III, Software and Product Integration Engineering
65M+
daly events processed
45x
more resource efficient
JU:NIZ ENERGY
“With InfluxDB Cloud Dedicated, the great thing is that we don't need to think about data storage costs or usage anymore because data storage gets way cheaper.”
Ricardo Kissinger
Head of IT Infrastructure and IT Security







